 One of the first thing we notice when we’re considering our options to guarantee our digital security; is the crazy amount of approaches; acronyms and functions to face and handle the different threats addressed to undermine our digital environments. Under such circumstances, it’s pretty easy to get lost and confused.
One of the first thing we notice when we’re considering our options to guarantee our digital security; is the crazy amount of approaches; acronyms and functions to face and handle the different threats addressed to undermine our digital environments. Under such circumstances, it’s pretty easy to get lost and confused.
In this post; we’re going to set the differences among them so to help you making the best choice for your guaranteeing your digital security; and keeping track on each capability before making your mind… or enhancing your current measures, if you need to do so.
The importance of semantics when protecting your Digital Environments
Regarding digital security, what is Threat Management?
According to PC Magazine, threat management is an umbrella term for the computer security and information security programs instituted within an organization (…).
In few more words, threat management describes the comprehensive view of software; digital footprints and behavior across networks addressed to manage whatever it happens and threatens the integrity of the digital security. Such comprehensive view includes Computer and Information Security, Risk Assessment and Integrated Threat Management.
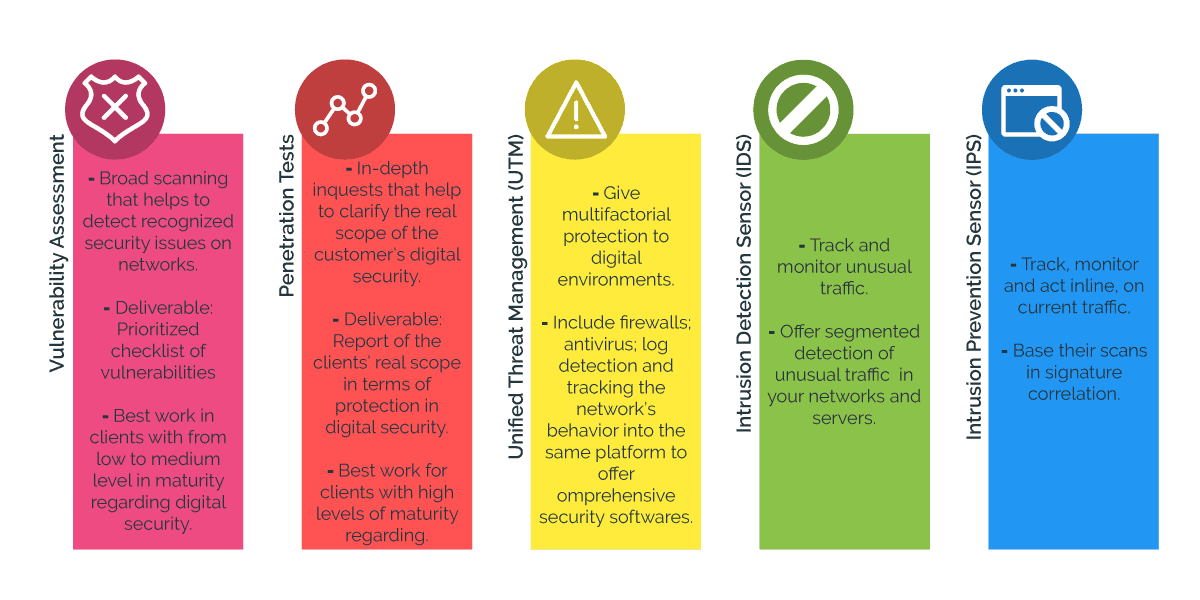
 Vulnerability assessment
Vulnerability assessment
On the one hand; vulnerability assessment covers a list of recognized vulnerabilities to detect security issues in the networks while reducing the timing to actually do it. Like this, we enhance our security levels while preventing and solving some events and attacks before they strike.
This comprehensive approach is addressed to and requested by customers aware of having vulnerabilities beyond their understanding; coverage and solution by traditional means, such as antivirus and firewalls.
Deliverables in vulnerability assessment tests consist in a prioritized checklist of vulnerabilities -and sometimes, their solutions- found in the clients’ digital environments obtained from a broad scanning. In this sense, vulnerability assessment could be useful as starting point to deeply diagnose the needs of protection of each network.
Penetration Tests
On the other hand; penetration tests are especial inquests to measure how efficient are the softwares and measures taken by the customers to protect their digital security. In order to do so, penetration tests simulate attacking targeted vulnerabilities on the customer’s digital environments.
 Notice that there’s a prerequisite to actually proceed with penetration tests: Customers have already implemented measures to give protection to their digital environments. So, they may have a clue on what are their vulnerabilities; and even predict what could they be their potential targets for intrusion.
Notice that there’s a prerequisite to actually proceed with penetration tests: Customers have already implemented measures to give protection to their digital environments. So, they may have a clue on what are their vulnerabilities; and even predict what could they be their potential targets for intrusion.
In short, penetration tests are in-depth inquests that help to clarify the real scope of their digital security; so to take corrective measures to strengthen them if necessary.
Related to deliverables in penetration tests; the main goal is giving a report of the clients’ real scope in terms of protection in digital security.
Unified Threat Management (UTM)
Third in this list, we have the Unified threat Management (UTM) solutions. The name refers to the combination of several components to give multifactorial protection to our digital environments. Such combination of elements include firewalls; antivirus; log detection and tracking the network’s behavior into the same platform to offer comprehensive security softwares.
 UTMs are relatively new in the market of solutions for protecting digital environments because their components usually were sold separately. This new approach gives to the customer the ease of dealing with one single vendor to guarantee integrative protection to its digital environments.
UTMs are relatively new in the market of solutions for protecting digital environments because their components usually were sold separately. This new approach gives to the customer the ease of dealing with one single vendor to guarantee integrative protection to its digital environments.
Additionally, UTMs simplify installation, deployment and upgrades for the customers and for this reason, they are a great option to give comprehensive protection to our digital environments. However, we always need the advice of the experts before choosing the best option in UTM.
Intrusion Detection Sensor (IDS)
Follow, we have the Intrusion Detection Sensors (IDS). As its name says, is a solution thought to detect intrusions. Simply viewed like this, then obvious question is; what kind of intrusions it detects?
The answer is equally simple: IDS detect whatever you need to detect in your networks, however, they won’t detect whatever it happens in the all context of your networks. In such regard, options are plenty and equally powerful; so you better determine in advance and with your vendor where is the best place for exploiting its benefits.
IDS have proven to best perform to track and monitor unusual traffic in specific segments of your networs. In other words, depending on the location you give to your IDS, you’ll be missing important signs and evidence of unusual traffic in other parts equally important into your digital environments.
Intrusion Prevention Sensor (IPS)
 Finally, we have the Intrusion Prevention Sensors (IPS). By their nature, they act similarly as IDS, but they go even further: IPSs track, monitor and act inline, on current traffic. Although this may result highly convenient, it has a spin off effect: It affects the traffic flow. Beside, as they only focus in incoming and outcoming traffic, is possible to miss events that passive scannings can easily detect.
Finally, we have the Intrusion Prevention Sensors (IPS). By their nature, they act similarly as IDS, but they go even further: IPSs track, monitor and act inline, on current traffic. Although this may result highly convenient, it has a spin off effect: It affects the traffic flow. Beside, as they only focus in incoming and outcoming traffic, is possible to miss events that passive scannings can easily detect.
IPSs base their scannings in security signature matching. For this reason, is imperative to properly define the way you program your IPS, so you don’t get drowned in false positives and upgrades that may interfere with other functions and actions to protect your digital environments.
In summary…
So, in summary, comparing Vulnerability Assessment, UTM, IDS & IPS as it follows:
Now that you have raised some veils regarding the abundant acronyms and approaches to guarantee you digital security; is the moment to give us a call to help you doing the best for protecting your digital environments.



