The digital world is an environment of opportunity for companies. For example, they can use an endless number of tools and channels to connect with customers that are even on the other side of the world.
However, just as there are opportunities, there are also cyber-attackers. These criminals are always ready to take any chance to illegally access the networks and websites of any unwary company.
One of the most innovative ways they’re using to access organizations’ systems is to exploit out-of-band vulnerabilities.
In this blog post, we’ll tell you what these vulnerabilities are and how you can prevent them from using the only solution available to address them.
What are the Out-of-Band vulnerabilities?
The Out-of-Band vulnerabilities, also known as OOB, are a series of alternative ways that an attacker uses to exploit a vulnerability that can’t be detected by a traditional HTTP request-response interaction.
This class of vulnerabilities is quite delicate and means very much to the security of a company, as cybercriminals can use them to their advantage. They’re mostly found in web applications and REST APIs.
Some of them are:
- Blind server-side XML/SOAP injection
- Blind XSS (delayed XSS)
- Host header attack
- Out-of-band remote code execution (OOB RCE)
- Out-of-band SQL Injection (OOB SQLi)
- Email header injection
- Server-side request forgery (SSRF)
- XML External Entity injection (XXE)
- OS Code injection: OOB
- XXE: Out of Band
How are Out-of-Band vulnerabilities exploited by cyberattackers?
To exploit an OOB vulnerability requires some techniques by a hacker as alternative ways to perform the attack.
 Consequently, criminals don’t get the output of the vulnerability in the direct response to the vulnerable request. Instead, the OOB techniques often require a vulnerable entity to generate an outbound TCP/UDP/ICMP request and that will then allow an attacker to exfiltrate data.
Consequently, criminals don’t get the output of the vulnerability in the direct response to the vulnerable request. Instead, the OOB techniques often require a vulnerable entity to generate an outbound TCP/UDP/ICMP request and that will then allow an attacker to exfiltrate data.
For example, in an OOB SQL injection, the information is obtained through a different channel than the one used to inject the SQL statement. In this case, it is injected through an email and obtained through the web interface.
However, the success of an OOB attack is based on the egress firewall rules i.e. which outbound request is permitted from the vulnerable system and the perimeter firewall.
How to identify Out-of-Band vulnerabilities through testing?
Also referred to as Out-of-Band application security testing or OAST. This is a procedure that relies on external servers to see vulnerabilities that otherwise would be invisible.
DNS technique
Using DNS is a common go-to technique to detect and exploit OOB vulnerabilities. For instance, OS Code injection, XXE, and SQL Injection can be detected by following a series of steps on DNS resolutions.
However, this process brings with it many limitations when it comes to putting yourself in the attacker’s shoes and imitating his actions. That’s why the following solution is the most recommended.
Acunetix’s AcuMonitor
Acunetix is a web vulnerability software capable of scanning any website and detecting vulnerabilities such as SQL Injection, Cross-Site Scripting, and XSS attacks.
This is an application that allows you to perform a constant scanning of your web environment through an easy-to-use interface and its powerful web vulnerability scanner.
Also, it provides you with access to well-structured statistics and reports. Such a feature is vivid proof to analyze the security evolution of your web applications, prioritize threats, and receive recommendations on how to fix security flaws.
Likewise, Acunetix provides the only technology on the market that can automatically detect Out-of-Band vulnerabilities. This feature is available within its main tool.
As a result, Acunetix advanced scanner works with a type of technology called AcuMonitor. This is the most sophisticated service that allows the tool to detect OOB vulnerabilities.
What is Acunetix’s Acumonitor?
AcuMonitor is an Out-of-Band vulnerability detection solution provided by Acunetix. This service is known for being automatically used by out-of-band checks and requiring no installation or configuration, only simple registration for on-premises versions.
What are the benefits of using Acunetix’s AcuMonitor?
This Acunetix solution is capable of increasing the scope of vulnerabilities that the Acunetix scanner can detect. In other words, if AcuMonitor technology didn’t exist, out-of-band detection wouldn’t be possible. Besides, vulnerabilities detected with AcuMonitor are NEVER false positives.
How does Acunetix’s AcuMonitor detect Out-of-Band vulnerabilities?
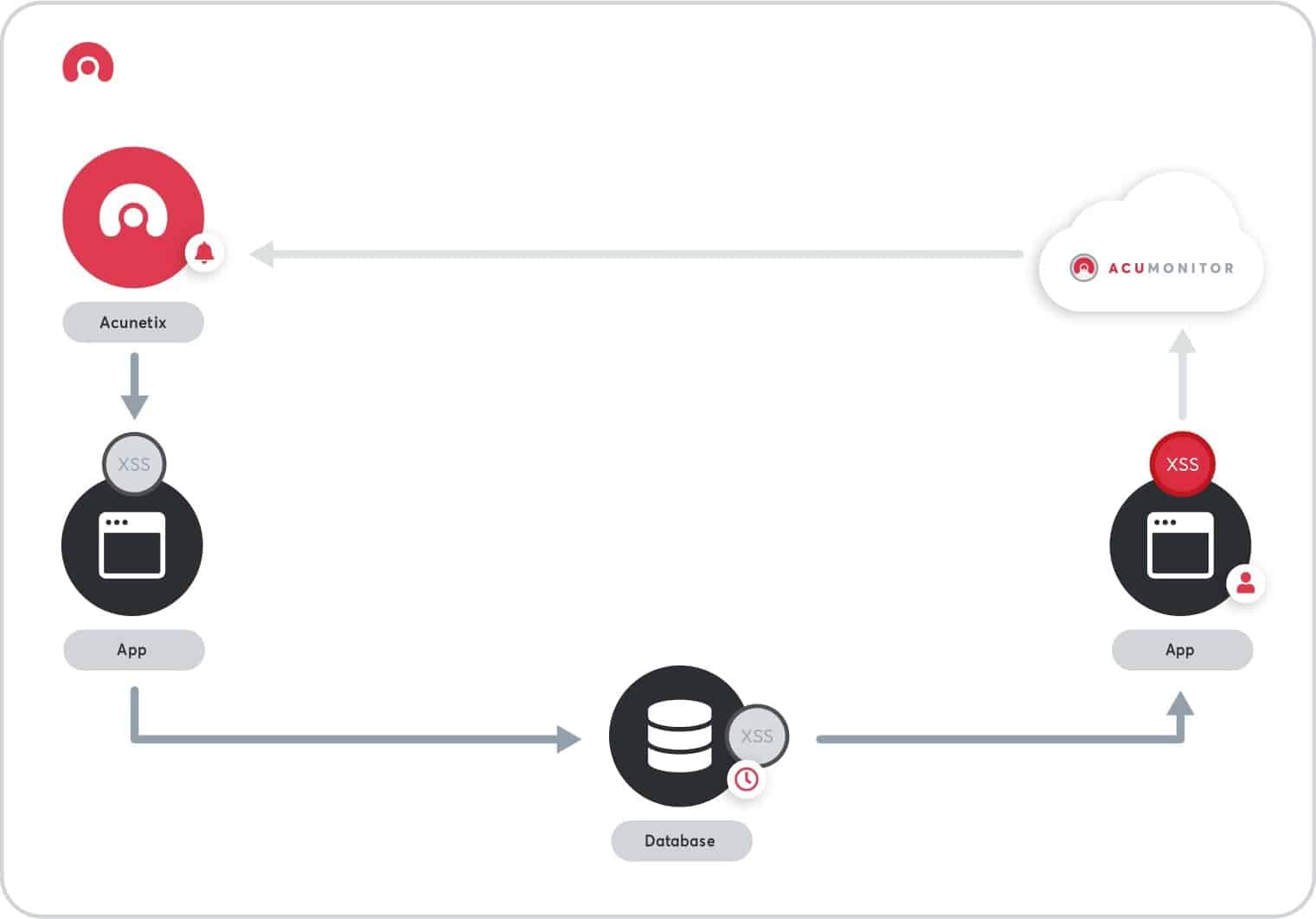
The moment you’re running the Acunetix scanner, it will send payloads to the tested application. When that occurs, that’s when the AcuMonitor features come into play.
- Firstly, AcuMonitor waits for two types of connections: connections from your web application after processing an Acunetix vulnerability payload and connections from your Acunetix scanner (online or on-premise).
- Then, Acunetix performs a test for an out-of-band vulnerability, the payload is designed to send a specific request to the AcuMonitor service. In the case of out-of-band vulnerabilities, this can happen either immediately or with a delay and from a different location in the application or from a completely different web application.
- Finally, your Acunetix scanner regularly polls AcuMonitor to check whether the payload has reached the service. If it has, it receives details from AcuMonitor, thus confirming the out-of-band vulnerability with 100% certainty.
Is Acunetix’s AcuMonitor a reliable solution to identify Out-of-Band vulnerabilities?
When it comes to detecting, there’s no safer software than Acunetix to find and get rid of them. AcuMonitor, as part of Acunetix, is a completely secure product that takes care of the process with both data transmission and data storage.
 For instance, AcuMonitor payloads use TLS whenever possible, which ensures that connections to AcuMonitor are encrypted. Besides, the tool doesn’t receive or store enough information to identify the source of the vulnerability.
For instance, AcuMonitor payloads use TLS whenever possible, which ensures that connections to AcuMonitor are encrypted. Besides, the tool doesn’t receive or store enough information to identify the source of the vulnerability.
On the other hand, the scanner doesn’t send any information about the original request to AcuMonitor.
Now, based on these terms, it will be difficult to distinguish between tests. Focus on your unique AcuMonitor ID acquired during registration and random unique identifiers generated by Acunetix.
Not convinced yet? Let us remind you that the requests made to AcuMonitor are saved only for a limited period of time with a maximum of 7 days. After that time, they’re deleted.
How can GB Advisors help you?
Managing to avoid the constant threats that exist within the digital environment can be a challenge. That’s why we attempt to help, advise, and accompany organizations like yours to strengthen their defense tactics. That way, lethal risks won’t be a problem at all.
If you suspect that your business is suffering from out-of-band vulnerabilities, don’t hesitate to contact our expert team as soon as possible. In this way, we will be able to provide you with a helping hand in this complex process.



