Today, technology is a fundamental part of any company’s operations. Therefore, addressing IT issues promptly is crucial to ensure operational continuity, maintain competitiveness in the marketplace, and protect the integrity of critical data.
In addition, the efficiency and security of IT systems directly impact all aspects of the business. This ranges from supply chain management to customer interactions.
We’ve created this blog to address the 5 most common and critical IT issues for these and other reasons. We give you some of the best solutions for you to drive business growth and innovation. Let’s get started!
What IT problems do businesses face in 2024?
All the issues listed below require businesses to take a proactive and well-informed approach to IT management. Doing so ensures that your technology infrastructure supports and promotes business strategy and long-term goals. Let’s take a look:
1. Lack of data backup
Data loss represents a serious problem for any company, regardless of its size. This inconvenience can originate from a variety of factors, such as:
- Human error
- Technical failures
- Natural disasters
The loss of critical data can result in significant financial losses, damage the company’s reputation, and undermine customer confidence. These effects underscore the importance of implementing robust backup and recovery strategies to protect business information.
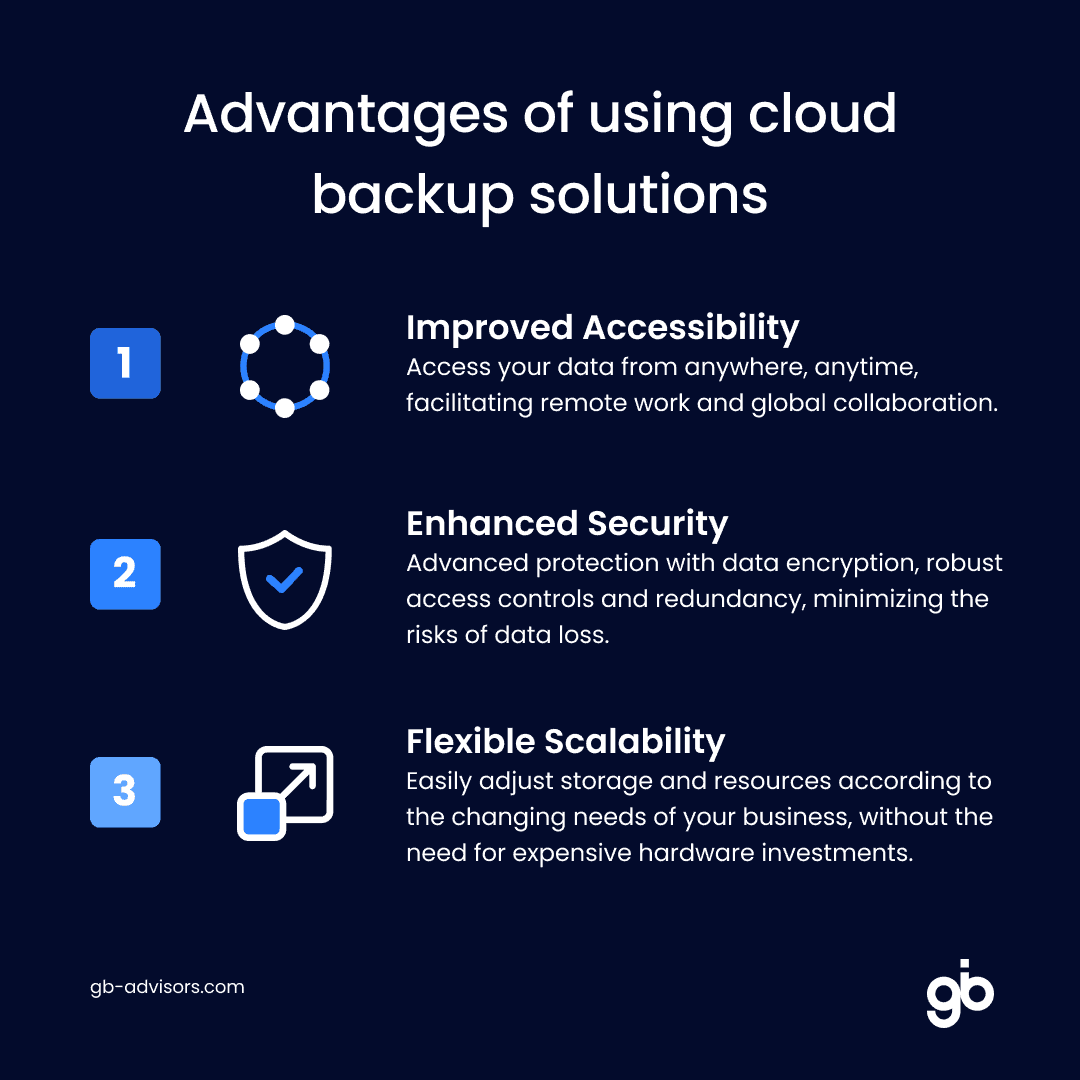
Solution: Establish automatic data backup policies and use the cloud
Implementing backup policies and technologies is critical to ensuring the security and availability of critical information. Here are several key components that enterprises should consider when developing a robust and reliable backup strategy:
- Defining clear policies: establish and document backup policies that detail what data should be backed up, how often, and who is responsible for overseeing these backups.
- Automate the backup process: Use backup software that automates the process. This reduces the manual workload and minimizes the risk of human error. This can include scheduling backups during non-business hours so as not to affect daily operations.
- Verification and testing of backups: implement regular procedures to verify the integrity of backups. It is necessary to perform data restoration tests and ensure that backups are functional and recoverable.
- Evaluate cloud provider options: Select a cloud service provider that offers reliable and secure backup solutions. Make sure it has a good reputation for data availability and security.
- Cloud storage implementation: migrating data backups to the cloud facilitates data recovery in the event of a disaster at the company’s physical location.
Compliance and security: Ensure that cloud backup solutions comply with industry- and regionally-relevant data privacy and security regulations.
2. Technical support problems
Technical support faces significant problems when adequate response times are not met. The lack of Service Level Agreements (SLAs) and Operational Level Agreements (OLAs) prevents effective monitoring and measurement of technical support performance.
In addition, the absence of necessary skills and adequate systems exacerbates the situation, resulting in decreased customer satisfaction, prolonged service interruptions, and inefficient management of resources.
Solution: SLA and OLA Implementation, Continuous Training and Ticketing Systems
We then developed 3 essential components to optimize the effectiveness of the technical support team: the implementation of SLAs and OLAs, continuous staff training, and the implementation of ticketing systems.
Implement SLA and OLA
For the definition and documentation of SLAs (Service Level Agreements), it is essential to identify the critical services that require timely technical support. This allows specific response and resolution times to be established, based on the criticality of the service and customer expectations. In addition, it is crucial to include clear and measurable metrics in the SLAs, such as mean time to resolution, fulfillment rate and customer satisfaction level, to evaluate technical support performance.
In implementing OLAs (Operational Level Agreements), effective coordination must be ensured by establishing OLAs between the departments involved in providing technical support that requires internal and external escalation, ensuring that everyone understands their roles and responsibilities. It is necessary to define response times similar to SLAs, which include specific times for the different teams to respond, as well as suppliers, and resolve their parts of the problem.
Skills development
Implement regular training programs for your technical support staff. Only then will you keep up with technological advances and customer expectations. These programs should cover:
- Technical training: train your team on new platforms, system upgrades, and emerging technologies that could be adopted.
- Troubleshooting: prepares staff on advanced troubleshooting methodologies. This allows you to improve diagnostic capabilities and troubleshooting efficiency.
- Practical simulations: incorporate real problem scenarios into training so that staff can practice in a controlled environment, improving their ability to respond under pressure.
Implementation of ticketing systems
Adopting an automated ticket management system is critical to efficiently manage support requests:
- Automatic registration and classification: automate the receipt and classification of tickets according to their urgency and type, so they will be handled in a prioritized and efficient manner.
- Real-time tracking: allows continuous monitoring of the status of each ticket. This prevents requests from remaining unresolved or getting lost in the process.
Transparency and communication
An effective ticketing system also improves communication between technical support and users:
- Constant updates: keep users informed about the progress of their requests. This helps manage expectations and maintain trust in the support process.
- User feedback: facilitate a channel for users to provide feedback on their support experience. This way you continuously improve the service.

3. Non-compliance with regulations and laws
Failure to comply with industry regulations and laws can have serious consequences for any company.
Regulatory violations can lead to financial penalties, litigation, and considerable damage to a company’s reputation. It can also erode the trust of customers, partners, and regulators, impacting business relationships and market opportunities.
Solution: Proactive approach to regulatory compliance
Organizations must take a proactive approach if they want to decrease their IT issues and mitigate the risks of sanctions and litigation. Let’s see:
Regular compliance audits
Internal audits are a vital tool for maintaining ongoing compliance. If planned and regular, audits help detect potential vulnerabilities or non-compliance before they escalate into major problems.
- Internal audits: conduct regular internal audits to review and assess adherence to legal and regulatory standards. By integrating audits as a regular practice, the importance of compliance is promoted among employees.
- External audits: In some cases, it may be beneficial to conduct external audits by independent third parties. This provides an objective assessment of compliance and enhances the company’s credibility with regulators and customers.
Automated CMDB and Asset Mapping
An essential element of regulatory compliance is the active and automated mapping of the CMDB (Configuration Management Database) along with infrastructure assets. It is crucial to keep this mapping constantly updated for audits. Automating this procedure ensures that asset information is kept up to date, which helps to identify critical components and assess relevant risks.
In addition, this automation facilitates the correlation of assets with incidents, problems, change management, and requests. Overall providing an effective record of activities that have impacted or altered an organization’s infrastructure and services.
Implementation of supporting technologies
The use of specialized compliance management software facilitates more efficient adherence to regulations:
- Process automation: these tools can automate the collection and analysis of necessary data. This is essential for compliance, reducing manual workload, and minimizing errors.
- Reporting: compliance software can generate detailed reports that are essential during audits and for regular monitoring of the compliance situation.
- Data security and privacy: ensure that the technologies implemented for personal data protection and information security are up-to-date and capable of preventing, detecting, and responding to security incidents.
4. Systems integration issues
Systems integration, one of the most common IT problems, poses challenges for organizations embracing new technologies. Incompatibility between new and existing systems can severely limit functionality and reduce operational efficiency. Consequently, information silos and discontinuous processes impair user experience and decision-making. Furthermore, these integration issues lead to increased manual workload, duplication of effort, and heightened risk of errors.
Solution: Facilitate integration through open standards and appropriate technologies
The ability to integrate different technologies effectively is crucial to maximize operational efficiency and improve the user experience.
Adopt open standards and APIs
Open standards are critical to ensure integration between different systems and technologies. By adopting these standards, companies can:
- Ensure compatibility: using globally recognized standards allows systems to communicate with each other without the need for custom solutions.
Facilitate expansion and scalability: It is easier to add or modify system components without disrupting existing operations with open standards. You gain greater flexibility to grow and adapt to new business needs.
APIs act as the glue that binds different systems and applications together, enabling seamless and efficient integration. Developing and implementing robust APIs, preferably RESTful or SOAP, is highly recommended for secure and efficient communication between systems.
Select platforms with high compatibility
Choosing the right software is vital for successful integration. During the selection process, it is important to:
- Review native compatibility: opt for platforms that support integrations with a wide range of applications and databases. Such as enterprise resource planning (ERP) systems that integrate CRM, finance, and supply chain functionality.
- Consider community and support: platforms with a large community of users, developers, and strong technical support are more likely to offer quick solutions to integration issues.
Compatibility testing
Before implementing a new solution, you’re going to need to:
- Perform extensive testing: this includes testing the integration in a controlled environment to detect and correct any problems before implementation.
- Use real-world usage scenarios: simulate day-to-day operations and high-load situations to ensure that the new software can run efficiently without disrupting existing operations.
5. System Downtime
System downtime can have devastating consequences for any business. Unexpected outages can halt production, affect business transactions, and damage the customer experience. These IT problems can result in significant losses in productivity and profitability.
Solution: Ensure business continuity
Here are three important solutions in this regard:
Alert generation associated with a specific infrastructure asset.
Implementing an alert generation system that is directly associated to specific infrastructure assets is crucial to minimize downtime.
- Detailed infrastructure mapping: Create an accurate inventory through tools that allow automated updating of all infrastructure assets, including servers, databases, applications, network devices, among others. This inventory should be integrated into the ITSM platform used.
- Association of assets to critical services: Each asset must be clearly linked to the critical services it supports. This facilitates the evaluation of the potential impact of any failure in the system.
- Configuration of intelligent alerts: Implement an alert system that uses detailed mapping to generate automatic notifications to support areas for effective action to enable resolution when problems are detected. These alerts should include specific information about the affected asset, the type of problem and its potential impact on critical services.
Implementing redundant systems
To prevent total system failure due to the failure of a single component, equip data centers with redundant hardware. This includes:
- Duplicate servers: have duplicate servers that can take over immediately if one fails.
- Network switches and connection paths: ensure that multiple data paths exist to avoid single points of failure.
- Replicated storage drives: maintain mirrored data on multiple storage devices to ensure continuous availability.
Business continuity solutions
Develop and maintain an effective business continuity plan that details how the organization will respond to and recover from different types of disruptions. This requires:
- Business Continuity Plan (BCP): develop and maintain a business continuity plan that includes specific strategies for minimizing downtime and recovering from different types of disruptions. This plan should be reviewed and updated regularly to adapt to changes in business and technology.
- Alternate data centers: establish and maintain alternate data centers or disaster recovery sites that can quickly take over in the event of an outage at the primary location.
- Monitoring and incident management tools: implement advanced system monitoring tools that can detect and alert abnormal conditions before they become serious problems. Combine this with an effective incident management system to ensure rapid problem resolution.

Conclusion
In conclusion, throughout this blog, we have explored five IT issues facing modern enterprises, along with effective strategies for solving them.
Final recommendations
- Conduct regular audits: Keeping a constant review of your IT systems is critical. Regular audits allow you to identify vulnerable or outdated areas that require improvement.
- Continuously train your team: make sure everyone is informed about security best practices and the efficient use of technologies. Ongoing training is an investment that improves the operability and security of the entire organization.
- Implement real-time monitoring tools: these tools allow you to act proactively before small problems escalate into critical situations, thus ensuring business continuity.
- Foster a culture of continuous improvement: involve your team in identifying opportunities for improvement and developing solutions. Celebrating achievements and recognizing individual and team contributions can foster a proactive culture dedicated to IT excellence.
We want to hear from you: Have you faced any of these IT issues in your organization? What solutions have you implemented?
If you’re looking for advice on how to say goodbye to all these problems, don’t hesitate to contact us. 😊



